I've released NAT Slipstreaming, a spooky new technique that allows an attacker to remotely access any TCP/UDP service bound to a victim machine, bypassing the victim’s NAT/firewall, just by the victim visiting a website. https://t.co/UlOnJPftTv Happy Halloween! pic.twitter.com/xorDXoh2uk
— Samy Kamkar (@samykamkar) October 31, 2020
You can read about it on Samy's website here;
Samy Kamkar - NAT Slipstreaming
exploit NAT/firewalls to access TCP/UDP services bound on a victim machine
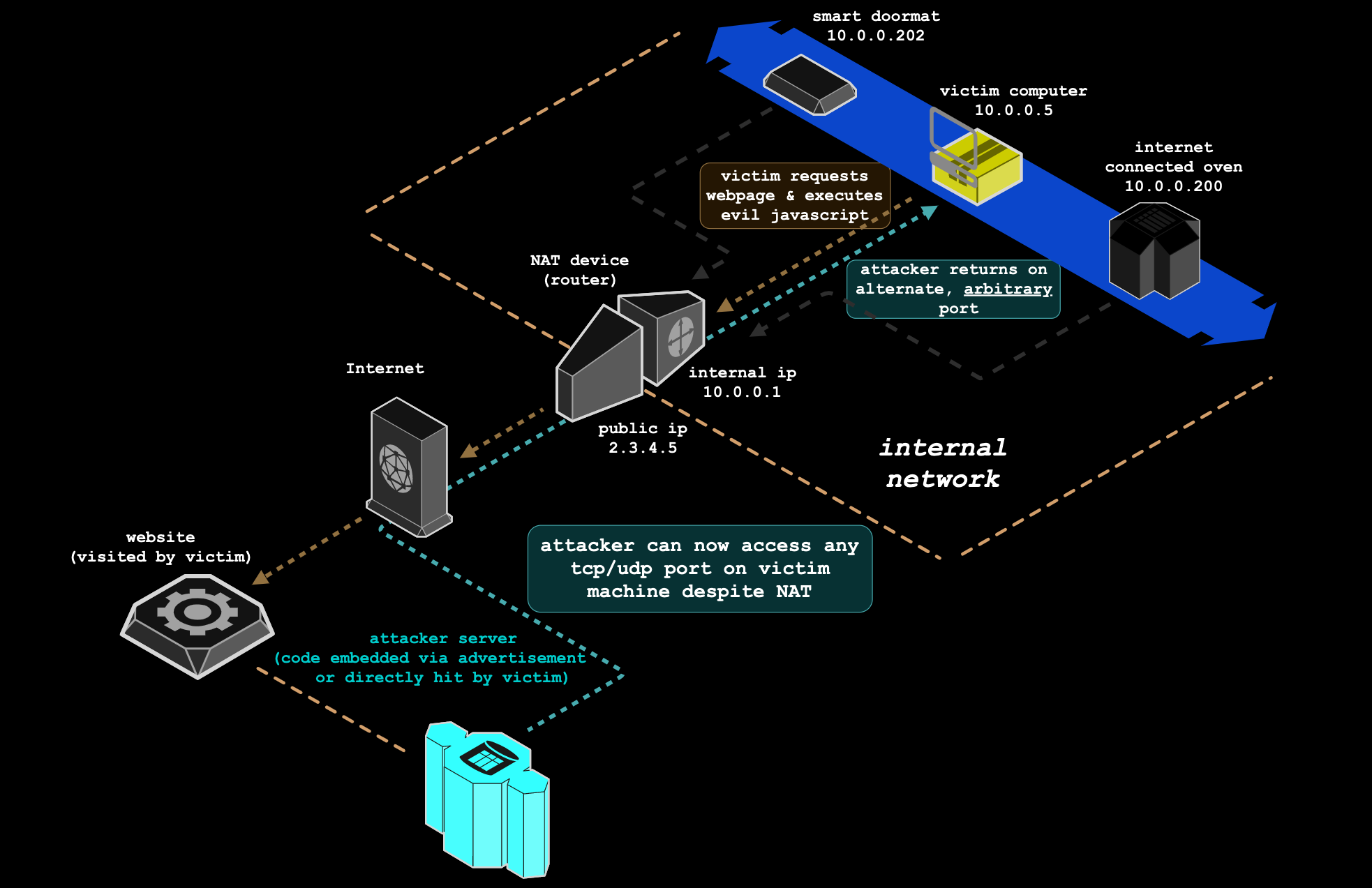
The repo is also hosted here on github;
samyk/slipstream
NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the victim’s NAT/firewall, just by the victim visiting a website - samyk/slipstream
